Don’t blame us for people suffering – London hospital hackers

The cyber criminals responsible for causing major disruption at London hospitals say they are “sorry for all the harm caused” but are “not to blame”.
The ransomware gang spoke to the BBC on encrypted chat service qTox attempting to justify the attack as a form of political protest.
Qilin, which has a well established record of attempting to extort money, claims in this instance it carried out a cyber attack as revenge for the UK government’s actions in an undisclosed war.
Experts are sceptical, however, with Jen Ellis, from the organisation Ransomware Task Force, telling the BBC that “cyber criminals like this gang lie routinely.”
“Where they are from and why they have carried out the attack is secondary to the harm being caused right now by patients and hospital staff,” she added.
The hack has led to more than a thousand operations and appointments being postponed and a critical incident being declared.
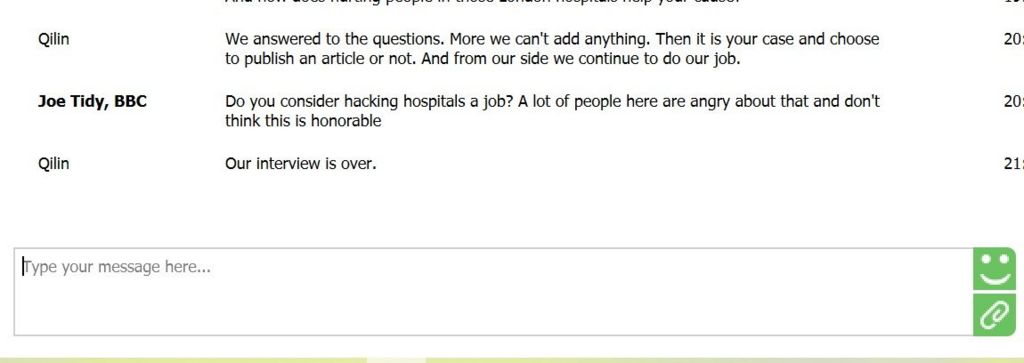
“Yes we know about the situation,” the hackers said, speaking in broken English.
“We are very sorry for the people who were suffered because of it. Herewith we don’t consider ourselves guilty and we ask you don’t blame us in this situation.”
The hackers said the UK government should be blamed as they were not helping in the unspecified war.
The gang, which is thought to be based in Russia, like many ransomware crews, would not say where it was.
It said the UK government “don’t even put a penny on the lives of those who fight on the front edge of free world,” which is reminiscent of language used to describe Ukraine’s fight against Russia’s invasion.
But it might also refer to Russian troops fighting against Ukraine.
The group says it chose to attack blood test firm Synnovis, which is used by two London NHS trusts, deliberately.
“Our citizens are dying in unequal combat from a lack of medicines and donor blood”, it said.
Researchers have previously said Qilin posted adverts for hackers to join its criminal service in Russian.
It would be unusual but not unprecedented for Qilin hackers to be in Ukraine, which has seen many alleged ransomware hackers arrested in recent months.
It’s very rare for hackers to be arrested in Russia as the government there refuses to cooperate with western law enforcement requests.
Qilin refused to be more specific about its political allegiance or geography “for security reasons”.
This is the first time that the crew has claimed to have a political motive for its hacks – Qilin has been tracked since 2022 in which time it has carried out criminal hacks against schools, hospitals, companies, councils and health care organisations.

The gang charges victims a ransom fee in Bitcoin to return systems to normal once they have infected a computer network or stolen private data.
On their darknet site, crew members regularly post details about their latest victims – of the dozens currently listed there are no others purportedly linked to political activism.
They have not yet posted the stolen data from Synnovis but threatened that they will soon: “Stay tunes”, they said.
The London hospitals hack was first announced on 3rd June when pathology service provider Synnovis said all its IT systems were offline.
It meant that blood tests and information sharing could not be carried out using the normal computerised systems.
The NHS trusts affected are Guy’s and St Thomas’ NHS Foundation Trust and King’s College Hospitals NHS Trust with patients affected in at 4 hospitals as well as GP services across Bexley, Greenwich, Lewisham, Bromley, Southwark and Lambeth boroughs.
One hospital doctor told BBC London that blood tests that once would have taken an hour could now take up to six hours, as the systems needed to process them are down.
According to NHS London, five planned C-sections were rescheduled and 18 organs were diverted for use by other trusts, while 736 hospital outpatient appointments and 125 community outpatient appointments had to be postponed.
Optional blood-borne virus (HIV, Hep C and Hep B) tests are also currently suspended.
Primary care appointments are going ahead as normal, but blood tests are being prioritised for urgent cases.
Synnovis says it is working to recover its IT systems and has not confirmed whether or not Qilin are holding it to ransom.
The BBC asked Qilin how they can justify harming innocent people they said “this interview is over” and have not responded since.
Related Topics
- Computing
- Cyber-crime
- Cyber-attacks
- Cyber-security
Published at Wed, 19 Jun 2024 11:23:21 +0000